LDAP: различия между версиями
Материал из noname.com.ua
Перейти к навигацииПерейти к поискуSirmax (обсуждение | вклад) |
Sirmax (обсуждение | вклад) |
||
| Строка 61: | Строка 61: | ||
==Check configuration== |
==Check configuration== |
||
| + | 2 steps to check configuration: |
||
| + | * chack with slapcat which shows data directly from files even if OpenLDAP server process is not running. |
||
| + | * Check with ldapsearch, which operate as ldap client. |
||
| + | |||
<PRE> |
<PRE> |
||
slapcat |
slapcat |
||
| Строка 100: | Строка 104: | ||
<BR> |
<BR> |
||
| − | Check admin passwod (connection to LDAP): |
+ | Check admin passwod (connection to LDAP with ldapsearch): |
| + | * user: <B>cn=admin,dc=demo</B> |
||
| + | * search base (:where to search from") <B>dc=demo</V> |
||
<PRE> |
<PRE> |
||
| − | ldapsearch -D "cn=admin,dc=demo |
+ | ldapsearch -D "cn=admin,dc=demo" -w r00tme -b "dc=demo"</PRE> |
| − | </PRE> |
||
Result: |
Result: |
||
<PRE> |
<PRE> |
||
| + | dn: dc=demo |
||
| − | # extended LDIF |
||
| + | objectClass: top |
||
| − | # |
||
| + | objectClass: dcObject |
||
| − | # LDAPv3 |
||
| + | objectClass: organization |
||
| − | # base <> (default) with scope subtree |
||
| + | o: demo |
||
| − | # filter: (objectclass=*) |
||
| + | dc: demo |
||
| − | # requesting: ALL |
||
| + | |||
| − | # |
||
| + | # admin, demo |
||
| + | dn: cn=admin,dc=demo |
||
| + | objectClass: simpleSecurityObject |
||
| + | objectClass: organizationalRole |
||
| + | cn: admin |
||
| + | description: LDAP administrator |
||
| + | userPassword:: e1NTSEF9akxUN0FaVGN2OGg4d0FPcHNQWHJPWG8wL3VleXJIaWs= |
||
| − | # search result |
||
search: 2 |
search: 2 |
||
| − | result: |
+ | result: 0 Success |
| − | # numResponses: 1 |
||
</PRE> |
</PRE> |
||
| − | |||
| − | Directory is empty, so search returns empty result |
||
| − | <BR> |
||
| − | |||
| − | |||
<B><So now we have OpenLDAP server with/B> |
<B><So now we have OpenLDAP server with/B> |
||
Версия 12:41, 24 марта 2016
LDAP
Нужна минимальная инсталляция LDAP для интеграции CD/CD инструментов - gerrit и jenkins
Assumptions
- Server IP: 192.168.56.102
- Server Name: cicd
- Root DN: demo
- Any password (for all users): r00tme
- OS: Ubunti 14.04
Подготовка
- add key
mkdir -p /root/.ssh /root/.ssh/authorized_keys
Установка пакетов:
sudo apt-get update sudo apt-get install slapd ldap-utils phpldapadmin mc vim strace tcpdump tcpflow
После установки
Check for running processes:
ps -auxfw <SKIP> openldap 3945 0.0 0.2 194060 8276 ? Ssl 11:24 0:00 /usr/sbin/slapd -h ldap:/// ldapi:/// -g openldap -u openldap -F /etc/ldap/slapd.d root 5073 0.0 0.7 241084 22484 ? Ss 11:24 0:00 /usr/sbin/apache2 -k start www-data 5076 0.0 0.2 241108 7324 ? S 11:24 0:00 \_ /usr/sbin/apache2 -k start www-data 5077 0.0 0.2 241108 7324 ? S 11:24 0:00 \_ /usr/sbin/apache2 -k start www-data 5078 0.0 0.2 241108 7324 ? S 11:24 0:00 \_ /usr/sbin/apache2 -k start www-data 5079 0.0 0.2 241108 7324 ? S 11:24 0:00 \_ /usr/sbin/apache2 -k start www-data 5080 0.0 0.2 241108 7324 ? S 11:24 0:00 \_ /usr/sbin/apache2 -k start
Настройка
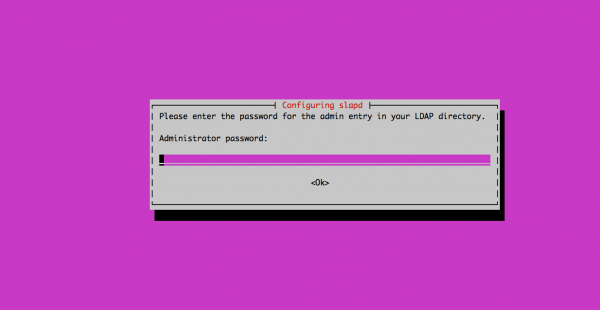
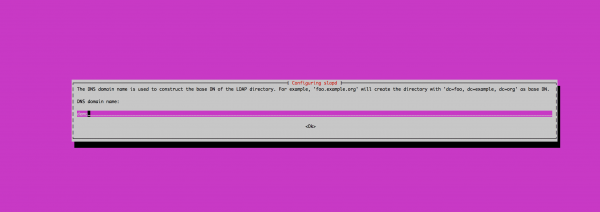
dpkg-reconfigure slapd
Configure root DN: demo for this demo.
Check configuration
2 steps to check configuration:
- chack with slapcat which shows data directly from files even if OpenLDAP server process is not running.
- Check with ldapsearch, which operate as ldap client.
slapcat
Result:
dn: dc=demo objectClass: top objectClass: dcObject objectClass: organization o: demo dc: demo structuralObjectClass: organization entryUUID: 2dd35bc8-85f2-1035-8d51-1b798eec3e6d creatorsName: cn=admin,dc=demo createTimestamp: 20160324095443Z entryCSN: 20160324095443.807089Z#000000#000#000000 modifiersName: cn=admin,dc=demo modifyTimestamp: 20160324095443Z dn: cn=admin,dc=demo objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9akxUN0FaVGN2OGg4d0FPcHNQWHJPWG8wL3VleXJIaWs= structuralObjectClass: organizationalRole entryUUID: 2dd3e822-85f2-1035-8d52-1b798eec3e6d creatorsName: cn=admin,dc=demo createTimestamp: 20160324095443Z entryCSN: 20160324095443.810666Z#000000#000#000000 modifiersName: cn=admin,dc=demo modifyTimestamp: 20160324095443Z
As you can see we have
- dn: dc=demo (root object)
- dn: cn=admin,dc=demo (admin user)
Check admin passwod (connection to LDAP with ldapsearch):
- user: cn=admin,dc=demo
- search base (:where to search from") dc=demo</V>
ldapsearch -D "cn=admin,dc=demo" -w r00tme -b "dc=demo"
Result:
dn: dc=demo objectClass: top objectClass: dcObject objectClass: organization o: demo dc: demo # admin, demo dn: cn=admin,dc=demo objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9akxUN0FaVGN2OGg4d0FPcHNQWHJPWG8wL3VleXJIaWs= search: 2 result: 0 Success
<So now we have OpenLDAP server with/B>
PHP LdapAdmin
Configuration
In file /etc/phpldapadmin/config.php change 2 lines:
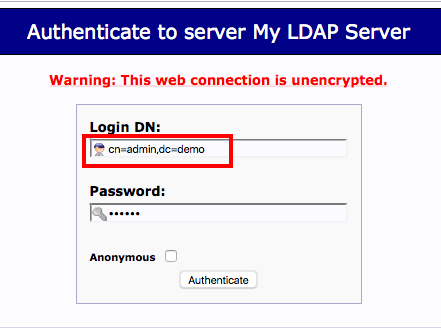
$servers->setValue('server','base',array('dc=demo'));
$servers->setValue('login','bind_id','cn=admin,dc=demo');
This changes are configured phpldapadmin to use correct root dn and default user.
Check
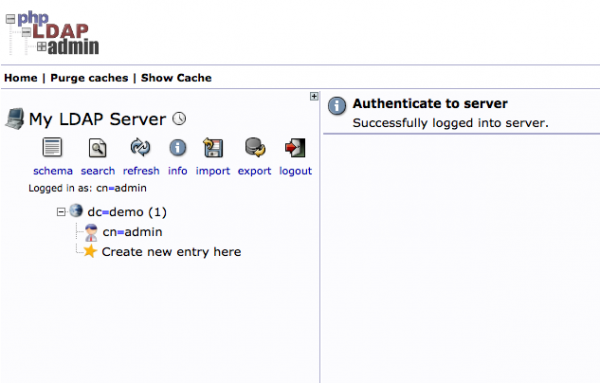
open in browser http://192.168.56.102/phpldapadmin/
Links
Jenkins
TBD
Manage Jenkins -> Configure Global Security --> LDAP