Jenkin Gerrit JJB: различия между версиями
Sirmax (обсуждение | вклад) |
Sirmax (обсуждение | вклад) |
||
| Строка 62: | Строка 62: | ||
jenkins-jobs: error: too few arguments |
jenkins-jobs: error: too few arguments |
||
</PRE> |
</PRE> |
||
| + | ==Configure JJB=== |
||
| + | JJB uses config file (defined with --conf option) |
||
| + | <BR> |
||
| + | For jenkins I'd like to have separate user with separate key, so let's generate rsa key, create user in ldap and add this user to group |
||
| + | <BR> |
||
| + | |||
| + | * Generate key: |
||
| + | <PRE> |
||
| + | #su - jenkins |
||
| + | |||
| + | $ ssh-keygen |
||
| + | Generating public/private rsa key pair. |
||
| + | Enter file in which to save the key (/var/lib/jenkins/.ssh/id_rsa): |
||
| + | Created directory '/var/lib/jenkins/.ssh'. |
||
| + | Enter passphrase (empty for no passphrase): |
||
| + | Enter same passphrase again: |
||
| + | Your identification has been saved in /var/lib/jenkins/.ssh/id_rsa. |
||
| + | Your public key has been saved in /var/lib/jenkins/.ssh/id_rsa.pub. |
||
| + | The key fingerprint is: |
||
| + | 99:6c:fb:38:1e:5c:05:c9:ba:d6:cf:9b:f2:db:f0:a6 jenkins@cicd |
||
| + | The key's randomart image is: |
||
| + | +--[ RSA 2048]----+ |
||
| + | | ... | |
||
| + | | o. | |
||
| + | | . . | |
||
| + | | ..o . | |
||
| + | | So. | |
||
| + | | ooo. | |
||
| + | | .+ o. | |
||
| + | | .+. o=. | |
||
| + | | .o..oE=o | |
||
| + | +-----------------+ |
||
| + | </PRE> |
||
| + | |||
| + | * Create user in ldap (same password as for all other users): |
||
| + | ** Jenkins user: |
||
| + | <PRE> |
||
| + | dn: cn=Jenkins User,ou=cicd,dc=demo |
||
| + | changetype: add |
||
| + | objectClass: top |
||
| + | objectClass: person |
||
| + | objectClass: organizationalPerson |
||
| + | objectClass: inetOrgPerson |
||
| + | cn: Jenkins User |
||
| + | ou: cicd |
||
| + | uid: jenkins-user |
||
| + | givenName: Jenkins |
||
| + | sn: user1 |
||
| + | userPassword: {SSHA}5oLdx/TJdGrRb3Jaz/9JWuFsj59pPoPt |
||
| + | mail: jenkins@jenkins.com |
||
| + | </PRE> |
||
| + | ** Add to group: |
||
| + | <PRE> |
||
| + | dn: cn=cicd administrators,ou=cicd,dc=demo |
||
| + | changetype: modify |
||
| + | add: memberUid |
||
| + | memberUid: jenkins-user |
||
| + | </PRE> |
||
| + | ** Run commands: |
||
| + | <PRE> |
||
| + | # ldapmodify < jenkins-user |
||
| + | adding new entry "cn=Jenkins User,ou=cicd,dc=demo" |
||
| + | </PRE> |
||
| + | <PRE> |
||
| + | # ldapmodify < add_jenkins_to_group |
||
| + | modifying entry "cn=cicd administrators,ou=cicd,dc=demo" |
||
| + | </PRE> |
||
| + | *Check in LDAP |
||
Версия 14:20, 25 марта 2016
Integration
Before start development, we need to configure Jenkins.
Jenkins Job Builder (JJB) takes simple descriptions of Jenkins jobs in YAML or JSON
format and uses them to configure Jenkins. You can keep your job descriptions in human readable text
format in a version control system to make changes and auditing easier.
It also has a flexible template system, so creating many similarly configured jobs is easy.
For our Jenkins jobs we will provide the following workflow:
- User creates JenkinsJob (yaml format)
- User commit job into gerrit cicd-jenkins-job repo and send it to review
- Jenkins trigger detects "review-created" event in gerrit and run syntax check job wich check yaml syntax
- If job success: Voite +1
- If job fails: Voite -1
- In case of "+1" human can review and add +1
- Merge
- Jenkins trigger detects "merge" event in gerrit and run update job
As result, job defined in yaml and commited to repo will be tested and created in Jenkins.
Create repo in gerrit
Create project, which inherits all permission:
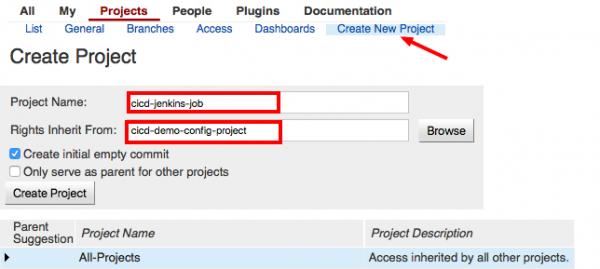
Install, configure and test JJB
Install
- Install pip and libs:
apt-get install python-pip python-yaml
pip install PyYAML python-jenkins
- Install JJB
git clone https://git.openstack.org/openstack-infra/jenkins-job-builder cd jenkins-job-builder/ python setup.py install
- Now JJB is installed
# jenkins-jobs
usage: jenkins-jobs [-h] [--conf CONF] [-l LOG_LEVEL] [--ignore-cache]
[--flush-cache] [--version] [--allow-empty-variables]
{update,test,delete,delete-all} ...
jenkins-jobs: error: too few arguments
Configure JJB=
JJB uses config file (defined with --conf option)
For jenkins I'd like to have separate user with separate key, so let's generate rsa key, create user in ldap and add this user to group
- Generate key:
#su - jenkins $ ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/var/lib/jenkins/.ssh/id_rsa): Created directory '/var/lib/jenkins/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /var/lib/jenkins/.ssh/id_rsa. Your public key has been saved in /var/lib/jenkins/.ssh/id_rsa.pub. The key fingerprint is: 99:6c:fb:38:1e:5c:05:c9:ba:d6:cf:9b:f2:db:f0:a6 jenkins@cicd The key's randomart image is: +--[ RSA 2048]----+ | ... | | o. | | . . | | ..o . | | So. | | ooo. | | .+ o. | | .+. o=. | | .o..oE=o | +-----------------+
- Create user in ldap (same password as for all other users):
- Jenkins user:
dn: cn=Jenkins User,ou=cicd,dc=demo
changetype: add
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
cn: Jenkins User
ou: cicd
uid: jenkins-user
givenName: Jenkins
sn: user1
userPassword: {SSHA}5oLdx/TJdGrRb3Jaz/9JWuFsj59pPoPt
mail: jenkins@jenkins.com
- Add to group:
dn: cn=cicd administrators,ou=cicd,dc=demo changetype: modify add: memberUid memberUid: jenkins-user
- Run commands:
# ldapmodify < jenkins-user adding new entry "cn=Jenkins User,ou=cicd,dc=demo"
# ldapmodify < add_jenkins_to_group modifying entry "cn=cicd administrators,ou=cicd,dc=demo"
- Check in LDAP